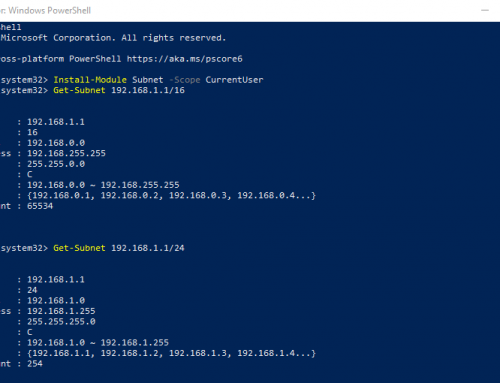
Powershell is an amazing tool for us Windows Administrators, It can be used to gather valuable information from Active Directory in seconds. I have began gathering a list of commands on this blog for common administration tasks and information gathering. Please feel free to leave any in the comments below and I will add them to the list. Keep this bookmarked also it will be continuously updated.
Adding the Active Directory Powershell Module
The commands in this blog will take advantage of the ActiveDirectory Powershell module. To add it run:
IMPORTANT: If you receive the error found here you will need to Import the Active Directory Powershell module. Instructions here.
Active Directory User Powershell Commands
Get a User and All Properties:
The * is a wildcard that will seclect all properties. Here you will replace username with the user you want to select, for example if looking for user JDoe: Get-ADUser JDoe -Properties *
Get a User and Select Certain Properties:
Using the | (pipe command) you can then select specific properties you would like to get. Here is a full list of available properties.
Get All Active Directory Users and Select Properties:
Here we find the name and login names for all users in Active Directory. Here is a full list of available properties.
Find Users with Password set to Never Expire:
Here we use a filter and where commands to find any users where the password is set to never expire and also where the account is enabled. That helps us filter out disabled accounts. I also used the replace command to clean up the results of the OU section. Here is a full list of available properties.
Find Disabled Accounts:
Will return any users in Active Directory that are set to disabled.
Find All Users that are Locked Out:
Will return any accounts that are currently locked out.
Disable User Account:
Run this command to disable a users account.
Enable a User Account:
Run this command to enable a users account.
Unlock a User Account:
Run this command to unlock a user account.
Find All Users with a Similar Property:
This command will find all Active Directory Users with the UPN like Contoso.com. So any users with that domain in their user principal name will be returned. Here is a full list of available properties.
Find All Members in a Security Group:
This command will find all users in an Active Directory Group. Edit GROUP NAME to your desired group and the Select portion to gather the information needed. OR Get-ADGroupMember -identity “GROUP NAME” | select name
Get All Users in an Specific OU:
This command will search Active Directory for a list of users in a defined Organizational Unit. Pipe it into a select command if desired.
Get All Accounts Expiring by a Set Date:
This will search AD for accounts set to expire by a certain date.
Get Expired Accounts:
Find any accounts in Active Directory that have expired.
Get Last Time Users Reset Password:
Gets a list of all User accounts in Active Directory and the last time the password was set. This can come in handy to find stale accounts. Be careful though, some may be old but set to password never expires.
Get All Users that Logged On in the Past 30 Days:
Get-ADUser -Properties LastLogonDate -Filter { LastLogonDate -gt $date } | Select-Object Name,SamAccountName,LastLogonDate
Command will get all users in Active Directory that have logged on in the last 30 days. Note this command must be done on 2 lines to use the variable.