With the exciting release of Azure Sentinel last week(release announcement), I decided to do some testing with the Preview.
If you missed the announcement, Azure Sentinel is Microsoft’s new Cloud Based Security Information and Event Management (SIEM) tool. Sentinel was built from the ground up and utilizes AI/Machine Learning to detect anomalies in your environment. Using AI algorithms it is said to significantly reduce the noise from a traditional SIEM product and help Security Engineers focus on important alerts.
Lets get into the setup steps for Azure Sentinel:
Setup Azure Sentinel Preview:
Login to the Azure Portal.
Search at the top for Azure Sentinel. Click Add to setup the Azure Sentinel workspace.
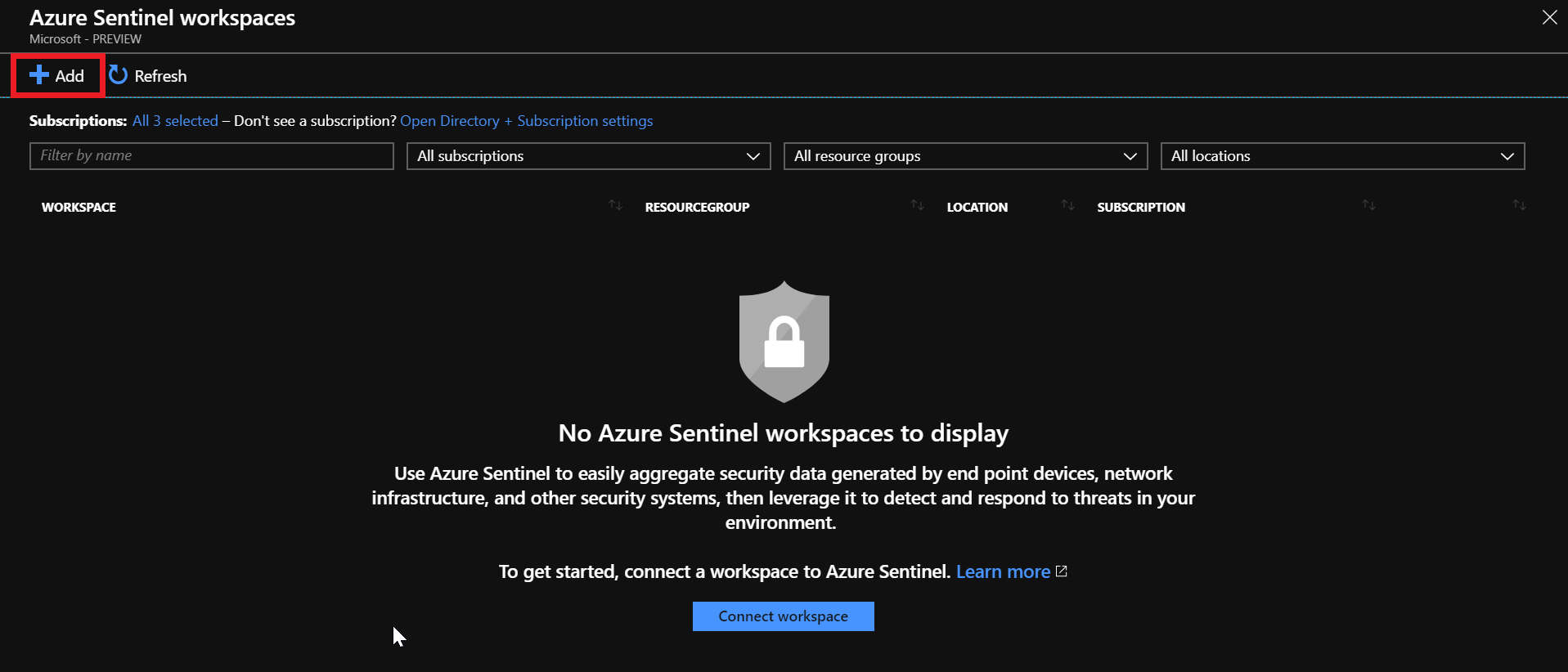
Click Create a new workspace. (You could also add to an existing one if desired.)
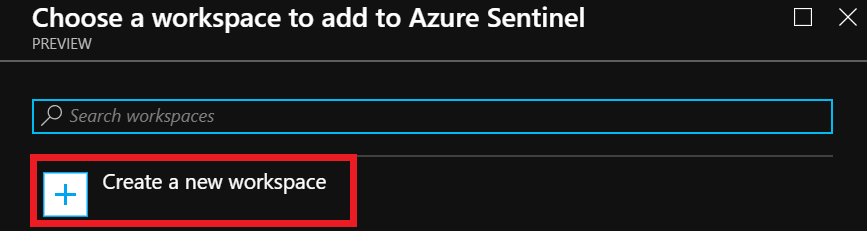
Name your new workspace and place in the proper Resource Group. NOTE: The Azure Sentinel Preview is currently Free. Microsoft states they will release pricing information at a later date. Be aware that you can still accrue charges with storage, throughput, and Machine Learning automation responses.
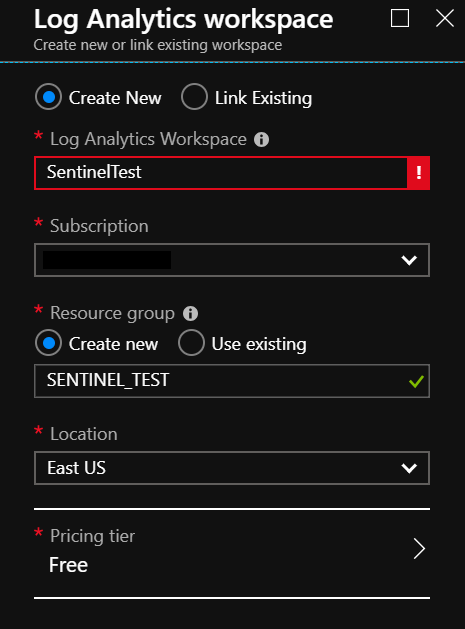
On the next page click the new workspace you created and click Add Azure Sentinel.
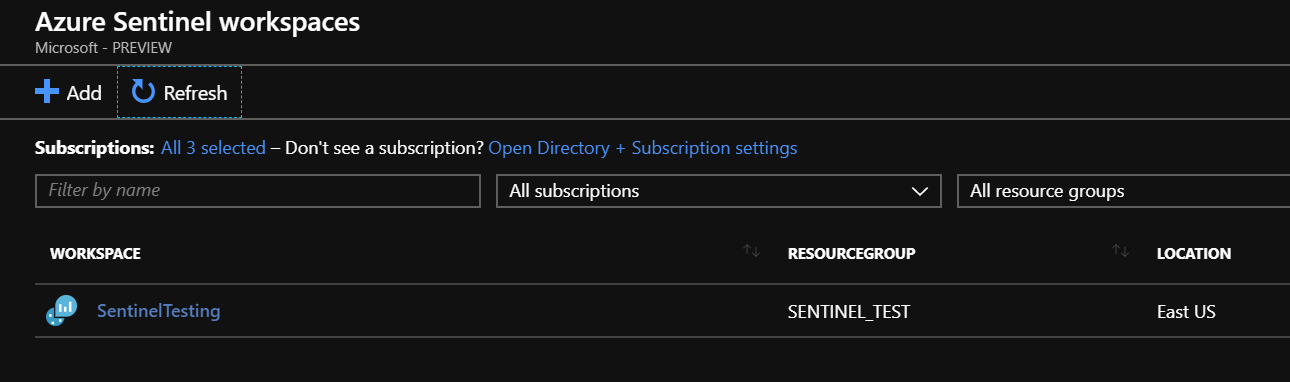
Click on the new workspace. Click the Getting Started tab and you will see the overview of the setup.
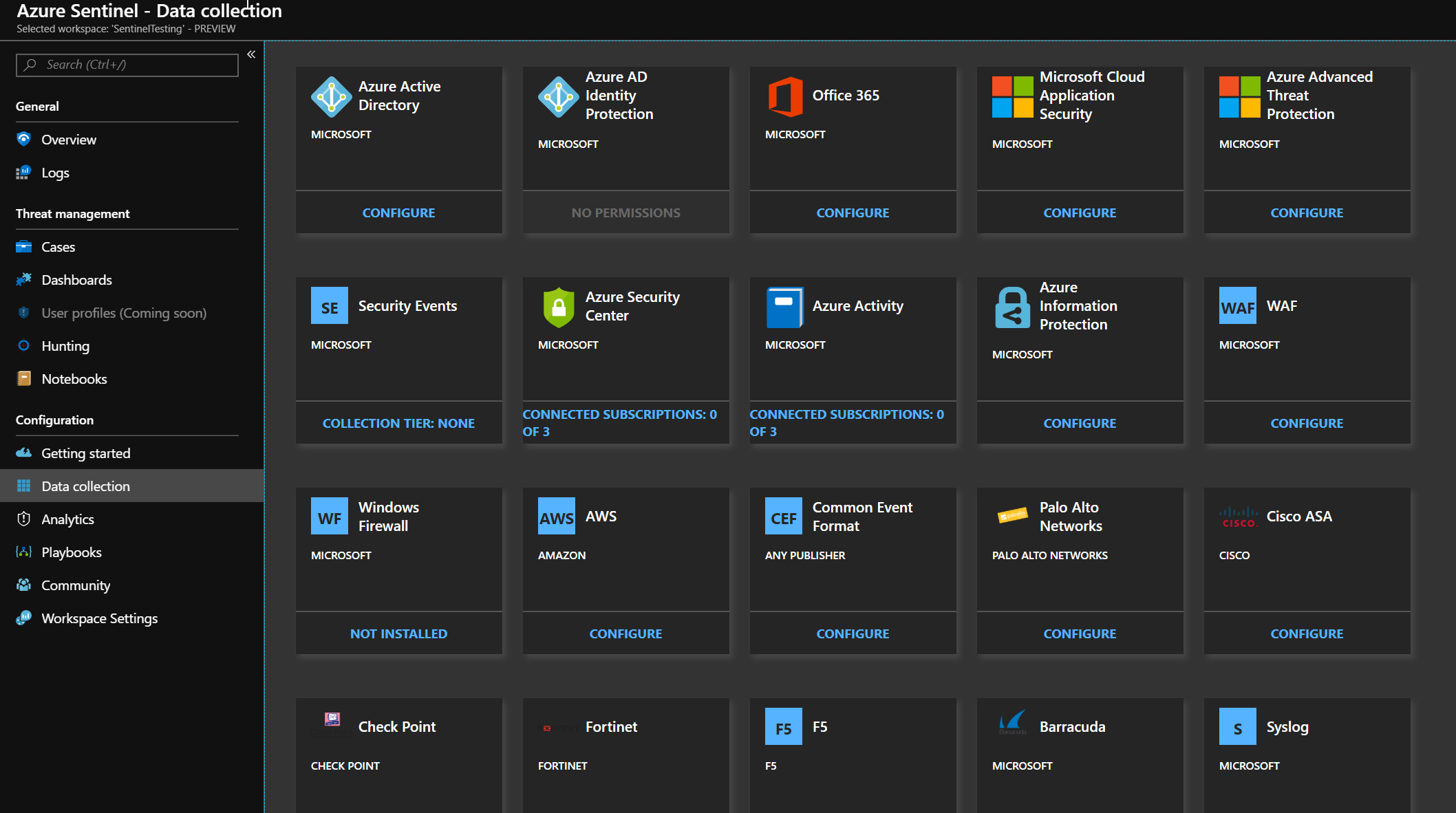
Setup Azure Sentinel Data Collection:
Click on the Connect for step 1 we will need to setup Sentinel to collect data from on-prem and cloud locations.
Out of the box it looks like Sentinel can integrate with many data collectors including:
Azure Active Directory, Azure Ad Identity Protection, Office 365, Microsoft Cloud Application Security, Azure Advanced Threat Protection, Security Events, Azure Security Center, Azure Activity, Azure Information Protection, WAF, Windows Firewall, AWS, Common Event Format, Palo Alto Networks, Cisco ASA, Check Point, Fortinet, FS, Barracuda, Syslog, DNS.
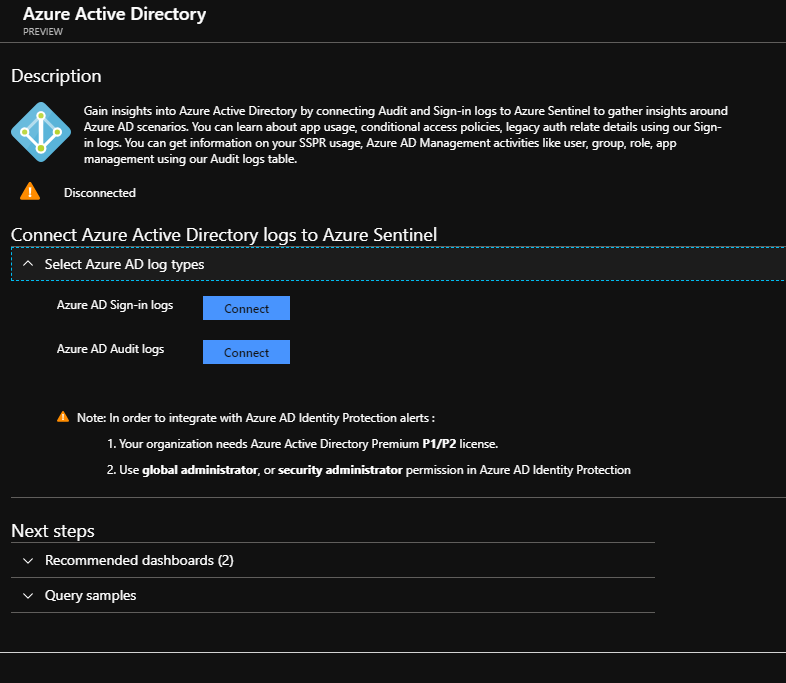
Click through any you wish to setup… each Data Collection plugin has step by step instructions. For example the Azure Active Directory was just 2 easy clicks to connect the logs. Some will be more involved and need you to point your current Syslog files or a client install.
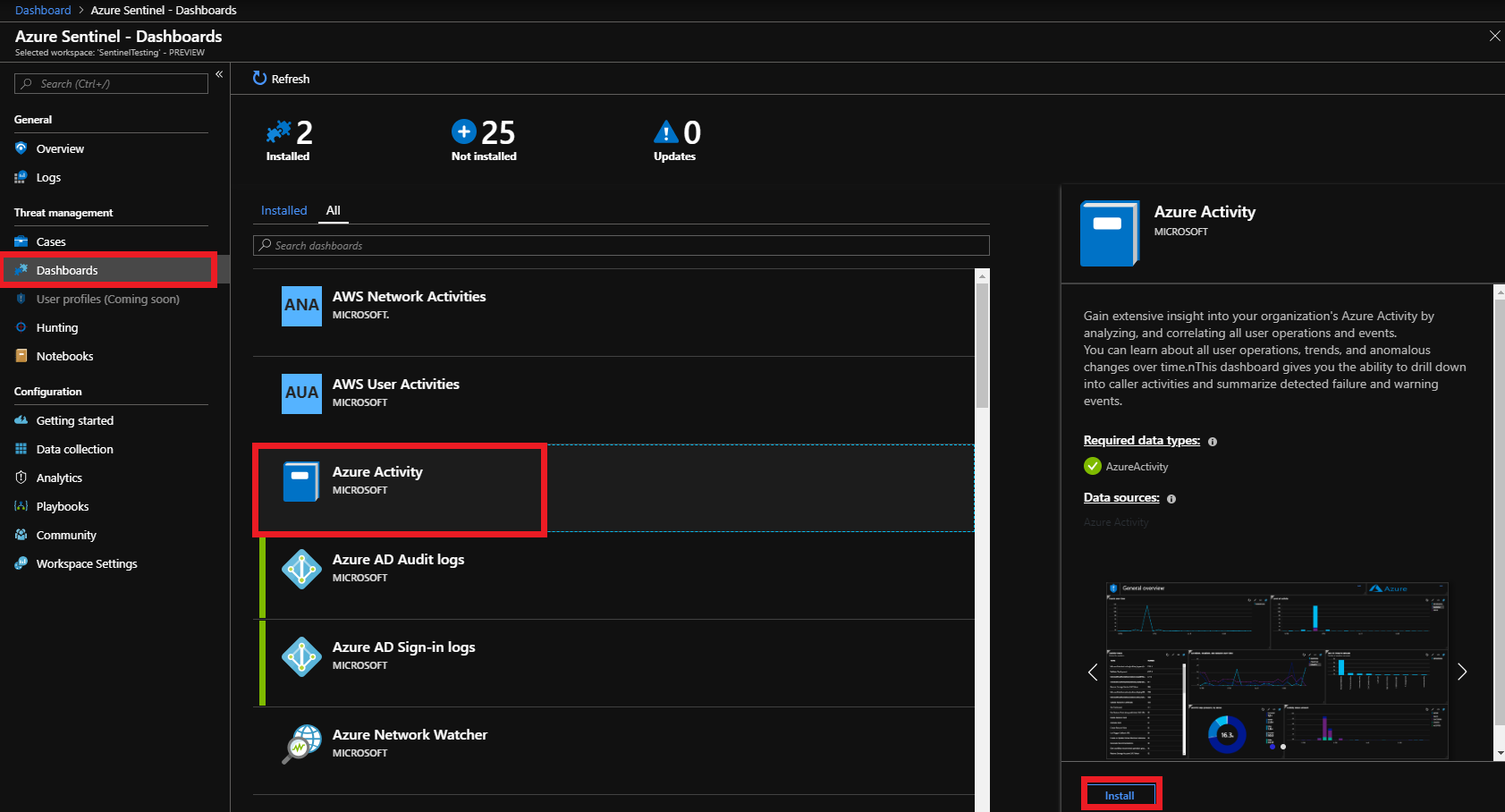
Setup Azure Sentinel Dashboards:
Once you have Data Collection setup go to Dashboards, select the pre-made dashboards for your Collectors and click Install on the bottom right. You can also customize dashboards, see details here.
Next we need to setup the Azure Sentinel Analytics.
Setup Azure Sentinel Analytics – Alert Rules:
Select Analytics and then Add.
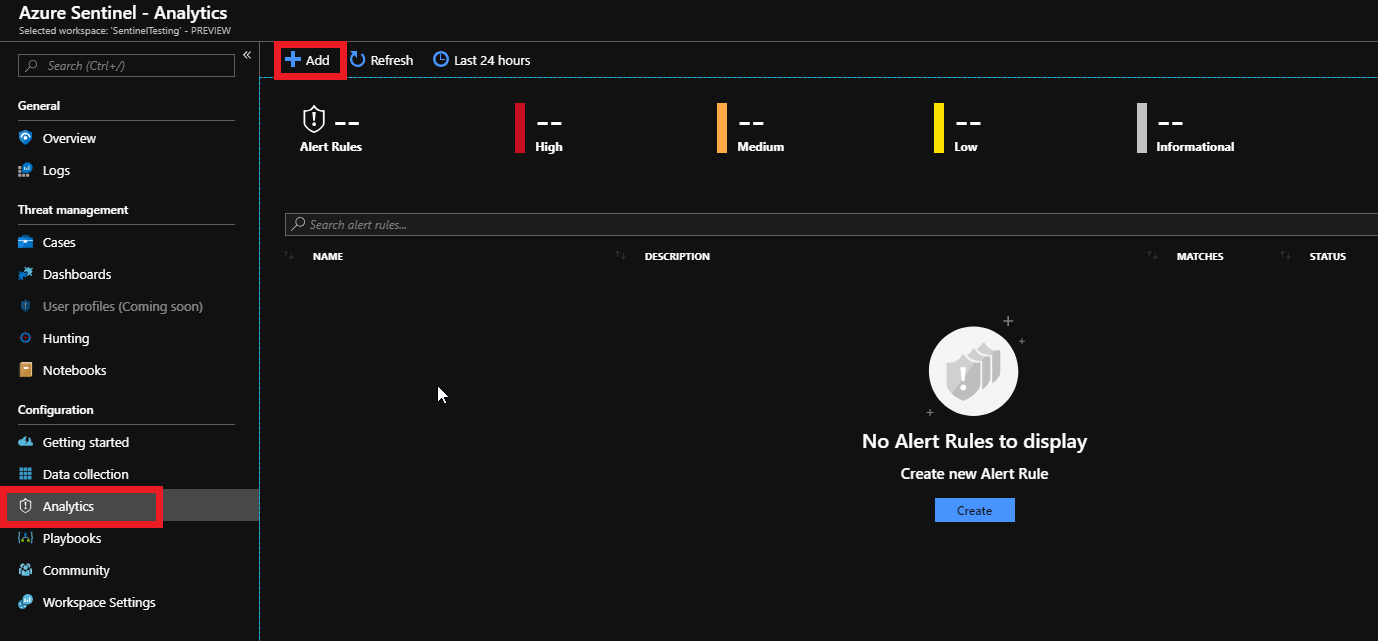
This is where i notice things get tricky… Microsoft does not appear to have a nice selection of pre-made rules. Admins will have to create their own alert rules using the query system. The example from Microsoft is shown here. I really hope they create some built-in best practice rules that can be easily enabled but it appears they plan to rely on the Community Section.
AzureActivity
| where OperationName == “Create or Update Virtual Machine” or OperationName == “Create Deployment”
| where ActivityStatus == “Succeeded”
| make-series dcount(ResourceId) default=0 on EventSubmissionTimestamp in range(ago(7d), now(), 1d) by Caller
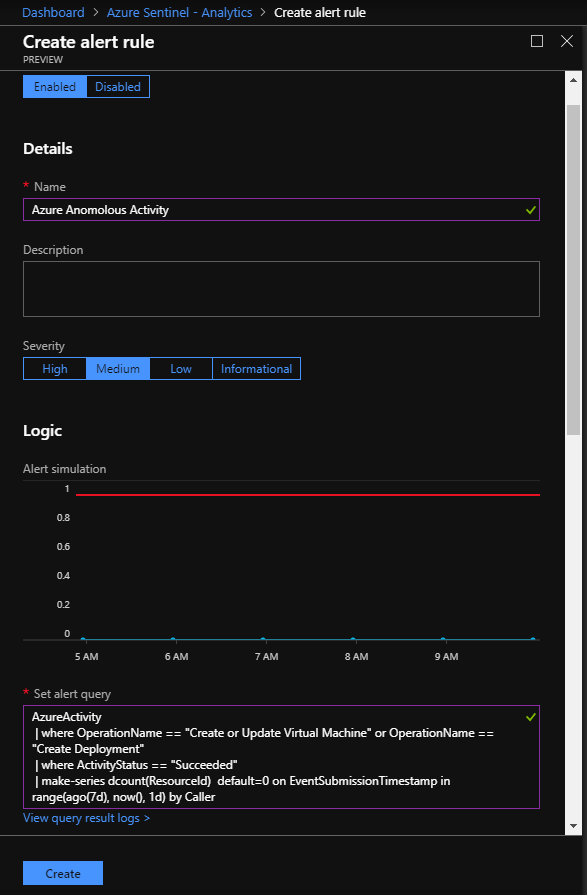
Click Create.
Next Select the Community tab under configuration and select Go to Azure Sentinel community.
From this community GitHub you can find many useful alerts to setup in you Azure Sentinel Preview.
From here we have Sentinel setup to collect data, view the dashboards, and trigger alerts. The next steps are to create Playbooks in response to these alerts. Playbooks will use Logic Apps and can be configured to open tickets, send messages to alert the security team and even use automation processes.
*More info to come as we experiment with the playbooks.
Enable Fusion:
Fusion is the AI/Machine Learning portion of Sentinel designed to help analysts with Alert Fatigue. More info here.
Open the Cloud Shell and select Powershell.
Create Storage and authenticate.
Run:
az resource update –ids /subscriptions/{Subscription Guid}/resourceGroups/{Log analytics resource Group Name}/providers/Microsoft.OperationalInsights/workspaces/{Log analytics workspace Name}/providers/Microsoft.SecurityInsights/settings/Fusion –api-version 2019-01-01-preview –set properties.IsEnabled=true –subscription “{Subscription Guid}”